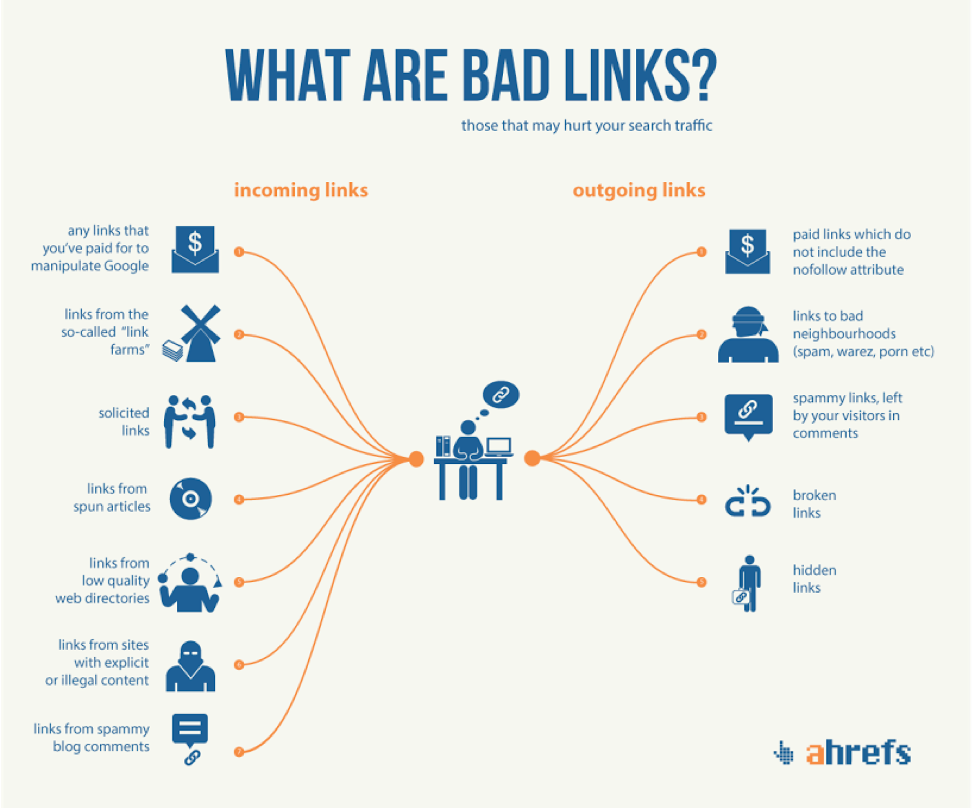
Cybercriminals running phishing operations are now making use of SEO specialists that break Google’s rules to get themselves placed above legitimate search results to lure victims.
Contents
- 1 Cybercriminals running phishing operations are now making use of SEO specialists that break Google’s rules to get themselves placed above legitimate search results to lure victims.
- 2 Why is Class 11 poisonous?
- 3 What is the purpose of SEO poisoning?
- 4 What is the most common goal of search engine Optimisation SEO?
- 5 What is the motivation of a white hat attacker?
Phishing site operators now use a special category of illegal search engine optimization tactics to show their pages above legitimate websites in search results.
Researchers from security firm Cybersixgill say these “Black Hat SEO” practices have become so popular that those who practice the skill are able to sell their services on dark web hacking forums for $70-500 per month. months to phishing site operators.
Unlike normal SEO techniques, which operate within the guidelines set by search engines, Black Hat SEO practitioners break rules set by Google and Microsoft to outwit the system and make phishing pages look better. listed.
Adi Bleih, dark web analyst at Cybersixgill, told SearchSecurity that some of the dirty tricks used by phishing attackers include keyword stuffing, redirecting links from other sites, and using paid links.
“The difference is that black hat SEO is a tactic used to rank a website that violates search engine guidelines,” Bleih said. “Legit SEO is all about creating the best result on the web, not just making it look like it is.”
As a result, phishing sites become much more effective at luring users to their pages and harvesting IDs and login information. Although sites run the risk of being caught and delisted by search engines for breaking SEO rules, the extra traffic is worth it to phishing site operators if properly balanced.
“In this case, it’s the actions of the threat actor that decide the lifetime of the domain,” Bleih explained. “If he uses black hat SEO techniques more often, he will be ‘punished’ by search engines and may be blocked or removed from search engine data.”
While the increased effectiveness of phishing attacks due to SEO is a threat in itself, the results also raise a larger issue for administrators and defenders. Cybercrime underground markets have now evolved to the point where specialized services are able to thrive as a support ecosystem for groups conducting large-scale cybercrime and fraud operations.
SEO poisoning has been used by cybercriminals in the past, most recently in a campaign to spread SolarMarker, an information stealer and backdoor. But Cybersixgill’s report said the practice is now widely available to a variety of threat actors and groups.
“That’s what happens in the world of phishing and scamming, where you can find actors who build packages of phishing sites — back-end and front-end development, admin panels, letters encrypted, etc. — and players who specialize in marketing and SEO,” Bleih said.
“This should be of concern to us – users who access different sites through search engine results.”
Dig Deeper on Data security and privacy
proxy hacking
SolarMarker malware spread through advanced SEO poisoning
Hack Friday: This Christmas, fight back against cyber criminals
Search engine poisoning: How are poisoned results detected?
Why is Class 11 poisonous?
CO has a stronger affinity for hemoglobin than oxygen. Due to this, the oxygen-carrying capacity of the blood is destroyed. This results in suffocation and ultimately death.
Why is CO toxic? Carbon monoxide is harmful when inhaled because it displaces oxygen in the blood and deprives the heart, brain and other vital organs of oxygen. Large amounts of CO can overwhelm you in minutes without warning – causing you to lose consciousness and suffocate.
Why is CO not poisonous in nature?
Indeed, carbon monoxide combines with the hemoglobin present in the blood cells of our body to form a stable compound called carboxyl-hemoglobin. This does not allow oxygen to be absorbed.
Is CO poisonous in nature?
Contention: Carbon monoxide is highly poisonous (poisonous) in nature. Reason: Carbon monoxide forms a stable complex with hemoglobin present in red blood cells.
Is CO poisonous to humans?
Carbon monoxide is a poisonous gas that has no smell or taste. Breathing it in can make you sick and can kill you if exposed to high levels. Every year around 60 deaths are due to accidental carbon monoxide poisoning in England and Wales.
Why carbon dioxide is not poisonous?
CO2 is not toxic; as a gas, CO2 itself will not harm you. This is an important fact to remember, as carbon dioxide is a vital part of the environment. The human respiratory mechanism revolves around CO2, not oxygen. Without carbon dioxide, humans could not breathe.
Why is CO called a poisonous gas Class 11?
Solution: Carbon monoxide is considered highly toxic because it combines with hemoglobin in the blood of a human body. It ultimately decreases the oxygen-carrying capacity of the blood.
Why is CO poisonous in nature?
Carbon monoxide (CO) is highly toxic to living beings. This is because it produces carboxyhemoglobin. When the concentration of this complex reaches about 3-4%, the oxygen-carrying capacity of the blood is greatly reduced.
Why is SEO is poisonous?
Carbon monoxide is highly toxic due to its ability to form a complex with hemoglobin. The CO-Hb complex is more stable than the O2-Hb complex. The first prevents Hb from binding to oxygen. Thus, a person dies of suffocation by not receiving oxygen.
Is SEO poisonous?
SEO poisoning, also known as search poisoning, is a method of attack in which cyber criminals create malicious websites and use search engine optimization tactics to make them appear prominently in search results.
What is the most common goal of SEO poisoning?
What is the most common purpose of search engine optimization (SEO) poisoning? A malicious user could create an SEO so that a malicious website appears higher in search results.
Does SEO poisoning require user interaction?
In this case, the SEO page will redirect to a final landing page based on user action, such as mouse movement or page rendering in the web browser. The crawler will not see the landing page redirect, as there is usually no user interaction or browser rendering involved.
What is the purpose of SEO poisoning?
SEO poisoning, also known as search poisoning, is a method of attack in which cyber criminals create malicious websites and use search engine optimization tactics to make them appear prominently in search results.
What is SEO in cybersecurity? Cybersecurity Search Engine Optimization (SEO) is a comprehensive online strategy involving SEO tactics and techniques that make the website more visible on search engines like Google and Bing.
Why SEO optimization is important?
SEO is made up of many elements, and knowing what they are and how they work is key to understanding why SEO is so important. In short, SEO is crucial because it makes your website more visible, which means more traffic and more opportunities to convert leads into customers.
What makes SEO successful?
Key factors for SEO success include optimizing the search experience, creating content for people (not search engines), and being voice search ready.
Why SEO is extremely poisonous?
Many SEO “kits” used by attackers (applications, usually written as PHP scripts, that generate poisonous pages to redirect site visitors to malicious sites) can mean the difference between a regular user visiting a website directly , someone who visits it from a search link and a search engine.
What is SEO poisoning in cyber security?
SEO poisoning, also known as search engine poisoning or search poisoning, is a method of attack that involves cyber criminals creating malicious websites and using several SEO tactics to get them listed prominently in search results.
Why is black hat SEO unethical?
Not only is black hat SEO considered unethical because it directly misleads users and search engines, but it also goes directly against Google’s webmaster guidelines.
What is the most common goal of SEO poisoning?
What is the most common purpose of search engine optimization (SEO) poisoning? A malicious user could create an SEO so that a malicious website appears higher in search results.
Does SEO poisoning require user interaction?
In this case, the SEO page will redirect to a final landing page based on user action, such as mouse movement or page rendering in the web browser. The crawler will not see the landing page redirect, as there is usually no user interaction or browser rendering involved.
What is SEO poisoning?
SEO poisoning, also known as search engine poisoning or search poisoning, is a method of attack that involves cyber criminals creating malicious websites and using several SEO tactics to get them listed prominently in search results.
What is the most common goal of SEO poisoning?
What is the most common purpose of search engine optimization (SEO) poisoning? A malicious user could create an SEO so that a malicious website appears higher in search results.
What is the most common goal of search engine Optimisation SEO?
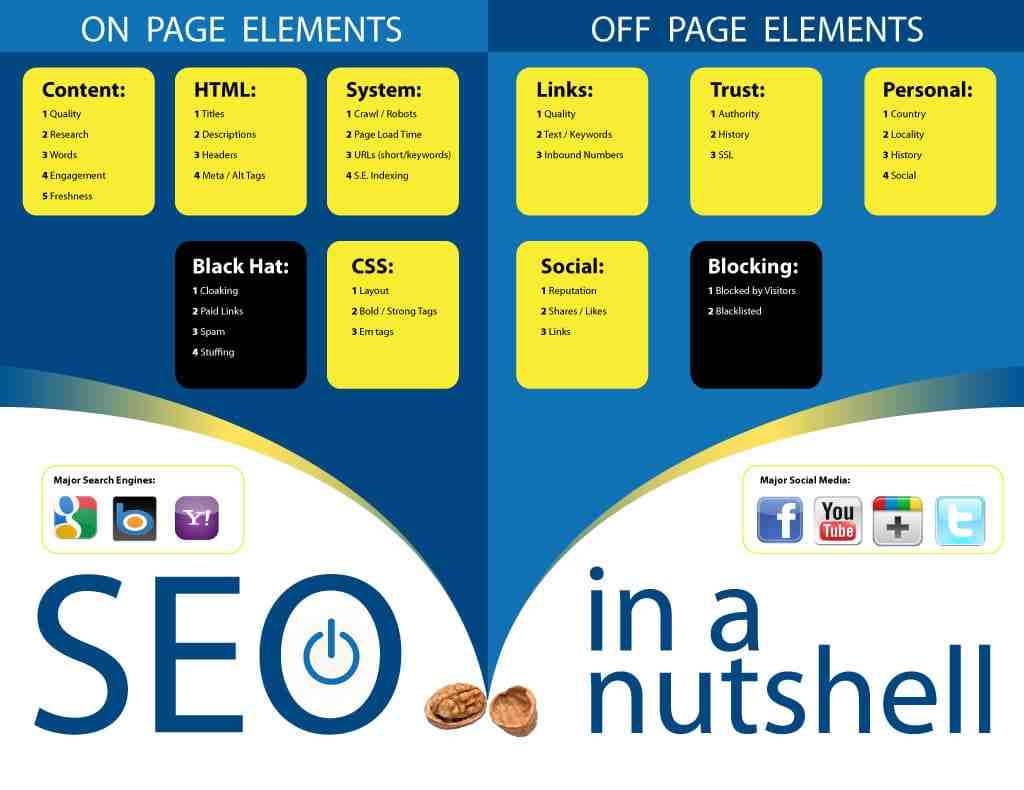
Search engine optimization (SEO) is a set of methods aimed at improving a website’s ranking in search engine listings, and could be considered a subset of Internet or web marketing. The main goal of SEO is to achieve higher search engine rankings, which in turn creates a larger target audience.
What Does SEO Search Engine Optimization Do? SEO stands for Search Engine Optimization and is the process used to optimize a website’s technical setup, content relevance and link popularity so that its pages can become easily findable, more relevant and popular for users’ search queries. , and as a result, search engines rank them better.
What is the most common goal of search engine?
What is the most common purpose of search engine optimization (SEO) poisoning?
- trick someone into installing malware or divulging personal information.
- to build a zombie botnet.
- overwhelm a network device with maliciously formed packets.
- to increase web traffic to malicious sites.
What is SEO poisoning?
SEO poisoning, also known as search engine poisoning or search poisoning, is a method of attack that involves cyber criminals creating malicious websites and using several SEO tactics to get them listed prominently in search results.
What is search engine optimization importance?
SEO stands for Search Engine Optimization. Simply put, good SEO optimizes your online visibility. This means that the more people see your website, the more your online traffic increases and the better your chances of providing your product or service to more people.
What is the motivation of a white hat attacker?
Explanation: White hat attackers break into networks or computer systems to discover weaknesses in order to improve the security of these systems. These burglaries are done with the permission of the owner or organization.
What are the three elements that make up the CIA triad, pick three? The CIA triad refers to an information security model composed of the three main components: confidentiality, integrity and availability.
Which method is used for data integrity?
Error checking and validation, for example, are common methods of ensuring data integrity within a process.
What are the types of data integrity?
Maintaining data integrity requires an understanding of the two types of data integrity: physical integrity and logical integrity.
What is data integrity used for?
In its broadest use, “data integrity” refers to the accuracy and consistency of data stored in a database, data warehouse, data mart, or other construct. The term – data integrity – can be used to describe a state, process or function – and is often used as an indicator of “data quality”.
What type of cyber attackers that makes political statements in order to create an awareness of issues that are important to them?
Criminals use the internet to try to steal money from a banking company. Explanation: Hacktivism is a term used to describe cyberattacks carried out by people considered to be political or ideological extremists. Hacktivists attack people or organizations they believe to be enemies of the hacktivist agenda.
What are the 5 types of cyber security?
Cybersecurity can be categorized into five distinct types:
- Critical infrastructure security.
- Application security.
- Internet security.
- Cloud Security.
- Internet of Things (IoT) security.
What is another name for confidentiality of information select one?
Explanation: Privacy is another name for privacy. Accuracy, consistency and reliability describe data integrity.
What type of attack allows an attacker to use a brute force approach?
The most basic brute force attack is a dictionary attack, where the attacker works through a dictionary of possible passwords and tries them all. Dictionary attacks start with some assumptions about common passwords to try to guess from the dictionary list.
What is a reason that internal security?
Why can internal security threats cause more damage to an organization than external security threats? Internal users have direct access to infrastructure devices.
What is a reason that internal security threats might cause?
To respond. Answer: Internal threats have the potential to cause greater damage than external threats because internal users have direct access to the building and its infrastructure devices. Internal users may not have better hacking skills than external attackers.
What three items are components of integrity of data choose three?
These three letters represent confidentiality, integrity and availability, otherwise known as the CIA triad.
What are the internal security threats?
Internal security threats can target either the citizens of the state or the organs and infrastructure of the state itself, and can range from petty crime to serious organized crime, political or industrial unrest or even domestic terrorism.